Background and Risks Associated with Various SCADA Systems

As we enter Industry 4.0, the fourth industrial revolution, past technologies used in the manufacturing or production infrastructure, called SCADA (supervisory control and data acquisition), are being merged with new technologies, called the Internet of Things (IoT), to enhance the ability of control and augmentation of the production environment. (Figure 1)
When IoT and SCADA systems are integrated to create an enhanced production environment, the system components can directly talk to each other, collect data and allow users remote access to these critical infrastructures. Compared to simple production platforms that existed in the past, this new advanced technology, or the Industrial Internet of Things (IIot), promotes many production benefits to include threats with the ability for hackers to harm critical systems within this new operational technology (OT) network from afar.
 |
| Figure 1: Evolution of the Production Environment1 |
SCADA systems can process data and be programmed to control certain functions on a centralized computer. SCADA systems have been used in various production infrastructures for over 50 years. SCADA is comprised of a computer and machine control to work in conjunction to collect data and present methods to control production processes. This now includes devices like remote telemetry units (RTU) to collect data and relay commands, and smart sensors and actuators to present real-time results and will ultimately communicate via the OT network.
Risks and Examples of SCADA System
Commercial Setting
SCADA systems are now becoming more common in some commercial applications to monitor and control the function of specific industrial type tasks. For example, swimming pool monitors function to take and regulate temperature readings, fill level and chlorine. (Figure 2) A chlorine meter takes automatic measurements and uploads the readings to a cloud server, which could be accessed by a terminal PC or smartphone.
This presents further scope for security concerns, as if any of these devices are compromised then the hacker may be able to read and even modify different parameters, illustrating the often-neglected security concerns of SCADA. It may seem trivial in comparison to an attack on vital infrastructure, however, someone with remote access may be able to turn up the chlorine and heating levels to waste resources, increase costs and potentially damage the equipment.
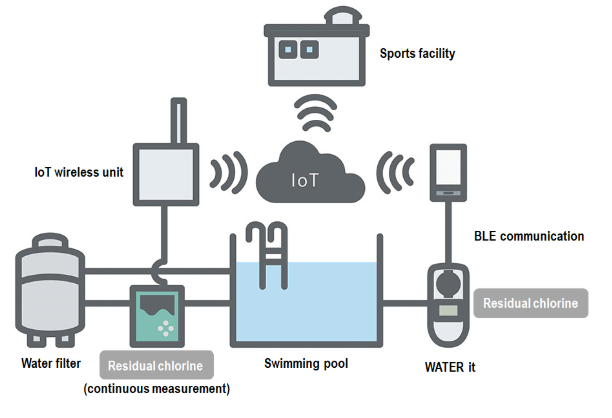 |
| Figure 2: Simple Swimming Pool Based SCADA System2 |
Industrial Setting
In an industrial setting, personal computers are commonly used outside of a plant so engineers can manipulate parameters from afar. In order to accomplish this, the OT environment will need to be interconnected with the typical information technology (IT) environment. While convenient for employees, the newly created connection points present an opportunity for anyone with the correct credentials, an IP address or compromised system to force their way into the IT environment and quickly move to the administrative areas of the SCADA unit.
Once a user connects as the admin on a computer network, they have access to all files and can easily modify and read the data contained therein. Just one terminal needs to be infected with malware for the attacker to laterally move until they can reach the SCADA system. After administrative access is gained on individual SCADA systems, any number of changes could be initiated that can damage systems, increase downtime, ruin product or exfiltrate production data.
Security and Solutions
SCADA systems are often designed without security in mind, as older systems required local access. The interconnectivity over the OT environment and recent SCADA technology improvements has made the entire production environment more susceptible to an attack.
Onsite and offsite backups could be flashed following an attack to resume pre-loss conditions. If the software that creates digital fingerprints of critical files and checks the integrity if a disparity is spotted, the corrupt files can be swapped out, leading to resuming the normal functions of the machines.
Many SCADA units are not adequately backed up and do not contain a tripwire to spot modifications to critical files which alter function. Catastrophic events may shut down a SCADA site and having backups at different locations or having mirrored SCADA machines, so if one is stopped, the other clone is placed into active mode and can halt this.
The Role of a Forensic Analyst
Forensic analysts can develop methodologies to investigate SCADA breaches by gathering schematics of the control system, monitoring and recording activity, and capturing malfunctions for analysis. A forensic analysis can help ascertain the type of incident, the root cause, mitigate any apparent holes and prevent a reoccurrence.
On top of determining the cause, forensic investigations can aid in the reinstatement to see what is needed to restart safely. Companies can then implement new measures such as ongoing monitoring, backups and tripwire to alert admins of any unusual activity and harden the system for future use.
1 BizIntellia. (2019). Industrial IoT vs SCADA: Which is More Powerful? Available: https://www.biz4intellia.com/blog/industrial-iot-vs-scada-which-is-more-powerful/
2 Optex. (2019). IoT Looking After the Water Quality of Swimming Pools. Available: https://www.optex.co.jp/e/solutions/pool-water-monitoring-iot.html.
Our experts are ready to help.



