Don't Geofence Me In: Have You Been Caught in a Google Location History Warrant?
You roll out of bed, prepare for work, help the kids get ready for school, and say your morning farewells. About the time you start your car, you receive the first notification for the day, "Light traffic to Starbucks this morning, approximately 15 minutes."
With technology so embedded into our daily lives, many have become desensitized to its implications on privacy. Some argue that modern life's hectic pace requires a mobile phone to act as a digital assistant, providing reminders, intel, document storage, and even location information. How else would you know if traffic allowed for a coffee before work?
For our mobile phones to be helpful assistants, they must collect data about us, and, unsurprisingly, they do. People today are aware that our phones track us now more than ever before. Perhaps you have heard how your cellular provider records your location data in Call Detail Records (CDRs) or how social media applications geotag pictures and videos with location information.
Most people are unconcerned about this, claiming they have nothing to hide. Why would I be concerned about the location data I generate if I do nothing wrong? Luis Molina, a man wrongfully charged with murder based upon geofence data, might have something to say about that.1 Molina's attorney, Heather Hamel, told the Phoenix New Times, "Police had arrested the wrong man based on location data obtained from Google and the fact that a white Honda was spotted at the crime scene. The case against Molina quickly fell apart and he was released from jail six days later. Prosecutors never pursued charges against Molina, yet the highly publicized arrest cost him his car, his job, and his reputation."2
Across the country, Google is utilized as evidence in many cases.3 However, the geofence warrants used to obtain this location data are being litigated against in many states.
What Are Geofence Warrants?
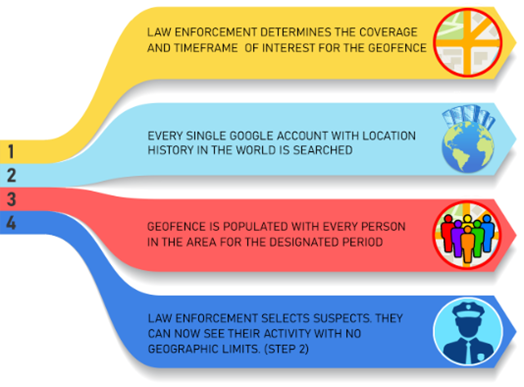
Google has responded to thousands of search warrants for geographical searches for all known users in the area, referred to as geofence warrants. The warrant requests Google to search its repository of user location data and turn that data over anonymously. These warrants set out a three-step process by which Google will search for location data on its users for a predetermined area and time.
The Three-Step Process in a Geofence Warrant
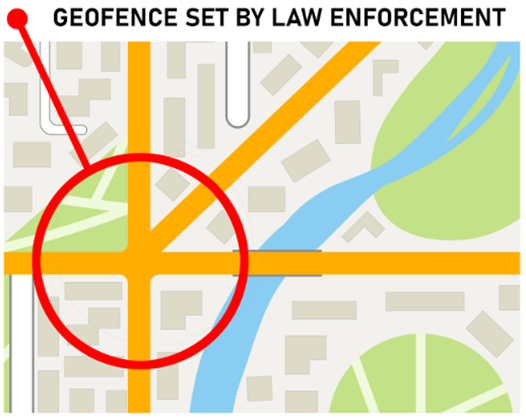
Step One: Google Sets the Geofence
Step one is a search limited by a geographical area or geofence. This is typically achieved by using a circle or square drawn using geographic coordinates. The search is also defined by time, which encompasses the incident being investigated. Google is instructed to search user data for location data that meets the time and geographic coordinates outlined in the warrant. Once this search is complete, Google returns the users’ data to law enforcement. At this stage, the data is advertised as anonymous data.
Google Location History Database Search
It is important to understand, limiting the size of the geofence has no impact on the number of users searched. This is because all location history data is stored in a single database. Since all of the data is stored in one container, the entire container must be searched to find the users’ data responsive to the warrant request.
The most unsettling part of this seems to be the indiscriminate search of users' data without their knowledge. In other words, Google needs to search every account with location history to conduct this search. Yes, you read that correctly, every account.
In documents from United States v. Okello Chatrie, Google representatives declared that every warrant requires a search of tens of millions of user accounts.4 To put that in perspective, Google responded to approximately 9,000 of these search warrants in 2018. That means a search of tens of millions of Google users' data occurred thousands of times. This type of search continues to this day.
Step Two: Google Provides Contextual Data for Law Enforcements to Examine
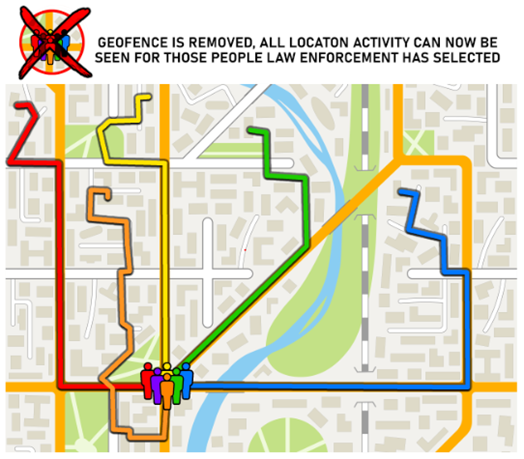
Law enforcement determines who they believe are the most likely suspects, and makes a request of Google to provide the contextual data on the step one users. Step two removes the geographical limits and expands the timeframe. This data now shows the step one users before and after they appear in the geofence. You will see the users as they travel from their homes, businesses, places of worship, or any other locations they visited that day. Finally, based on this data, law enforcement will select the users they believe are suspects or associated with the incident and make the final request.
This geofence search warrant process yields private location data about all the parties captured in the search. In step two, users can be tracked when traveling to protected places they frequent in their daily lives. These unique movements are not anonymous but are very identifiable. Think about each place you have been today. What is the likelihood of another person, besides a close family member, going to each of those places simultaneously? Imagine you were caught inside a geofence in the morning. Later that day you visit your doctor, grab lunch with a love interest, pick your kids up from school, and meet up with friends for a drink that evening before calling it a day. All that activity would be recorded.
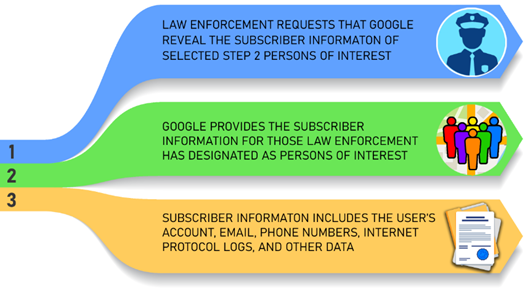
Step Three: Google Reveals Your Subscriber Information to Law Enforcement
Step three is the final request made based on a geofence warrant. Law enforcement will request step two users and have Google reveal their subscriber information. This may include the subscriber's Gmail address, telephone number, account number, Google services used, and internet protocol logs associated with the account. This is the "de-anonymization" of the user(s).
Have I Been Targeted By a Geofence Warrant?
In many instances, these warrants are accompanied by non-disclosure orders that limit Google from notifying its subscribers when their data has been turned over. When a non-disclosure order is not provided, Google has notified targeted users by email. Zachary McCoy of Gainesville, FL received a notification as a result of a geofence warrant that targeted suspects of a burglary in his own neighborhood.5 "I didn't realize that by having location services on that Google was also keeping a log of where I was going," McCoy stated. "I'm sure it's in their terms of service but I never read through those walls of text, and I don't think most people do either." McCoy was determined not to be the suspect as a result of the investigation.6
Caleb Kenyon, Attorney at Turner, O'Connor, Kozlowski who represented Mr. McCoy, shared his opinion on geofence warrants and stated, "Geofence warrants are law enforcement's latest machinations to harness data harvested by big tech and claim that they aren't conducting a search. But a government entrance through the back door to search your data is still a search under the Constitution. The general geofence warrant fails on multiple fronts: it lacks probable cause for all persons searched and it lacks particularity in the discretion allowed during the execution of the warrant."
Litigation against the use of this technique is heating up. Cases across the nation are receiving attention from the media and Fourth Amendment arguments are at the heart of these cases. The National Association of Criminal Defense Lawyers (NACDL) and the Electronic Frontiers Foundation (EFF) have assisted defense attorneys in litigating these issues. The obvious over-breadth and lack of particularity are among the arguments against the use of these warrants.
Sources:
2 Avondale Man Sues After Google Data Leads to Wrongful Arrest for Murder | Phoenix New Times
3 https://support.google.com/accounts/answer/3118687?hl=en
4 https://www.nacdl.org/Content/United-States-v-Chatrie,-No-3-19-cr-130-(E-D-Va-)
Vores eksperter kan hjælpe dig!